Please share to your friends:

You may also like
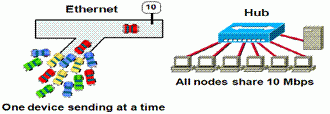
Early Local Area Networks The earliest Local Area Network technologies that were installed widely
Early networks From a historical perspective, electronic communication has actually been around a long
Intranet VPNs: Link corporate headquarters, remote offices, and branch offices over a shared infrastructure
User Authentication with Kerberos Kerberos is another technology. It is one that has been
There are a few different types of firewalls. Here’s a little history. The traditional
There are real technology implications to these new Internet applications. First is the need